
Your devices could be mining cryptocurrency without your knowledge. Right now.
It’s called cryptojacking, and many cybercriminals have turned to this insidious practice because of the rising popularity of cryptocurrencies and the lure of profit from crypto mining.
Cryptojacking is the illegal process of stealing a device’s computational power to mine cryptocurrencies without the user’s knowledge or permission.
Today, we have more than 20,000 cryptocurrencies in the world, valued at more than a trillion dollars. Mining these cryptocurrencies is a money-minting process. It offers lucrative returns, but it’s no easy task. It requires hardware, uninterrupted electricity, and huge computational power.
One way cybercriminals overcome this problem of crypto mining is cryptojacking. They reap the reward, but you pay the cost without even realizing it.
To defend against cryptojacking, you have to strengthen your cybersecurity program. You should use software like antivirus protection, runtime application self-protection (RASP) software, and web application firewalls (WAF) solutions. But to fix robust security defenses, it’s crucial to understand cryptojacking in detail.
And that's what we'll try to help you do with this article. We'll explore the dark world of cryptojacking and take a closer look at how it works. We’ll also learn how to detect cryptojacking attempts and what you can do to protect your devices from falling prey to this sneaky and costly cybercrime.
Before we dive deep into cryptojacking, let’s start with the basics of cryptocurrencies and crypto mining. This is important for understanding how cryptojacking works.
In 2009, one mysterious developer named Satoshi Nakamoto mined Bitcoin, the first-ever digital currency. Fast forward a decade, and the cryptocurrency market is booming.
Definition of cryptocurrency: Cryptocurrency, sometimes called crypto-currency or crypto coins, is digital money built on blockchain technology and secured by cryptography. It is decentralized, meaning no central authority or banks regulate it. However, all transactions are encrypted, stored, and recorded in a public database through blockchain technology.
Nowadays, we have cryptos like Ethereum, Tether, Solana, BNB, XRP, and even Dogecoin, apart from the much sought-after Bitcoin. Crypto enthusiasts consider crypto coins extremely valuable, resulting in soaring cryptocurrency prices since the early Bitcoin days. Such high prices made crypto mining, the way to earn cryptocurrencies, extremely lucrative.
Definition of crypto mining: Crypto mining or cryptocurrency mining is the process of creating new digital coins by verifying and adding blocks to an existing blockchain. Here, verifying and adding blocks involve solving complex cryptographic hash equations. The first miner to crack the puzzle gets mining rewards like newly created cryptocurrencies or transaction fees.
This process of guessing the hash requires using computational power. The more profitable a cryptocurrency is, the more difficult the hash is, and the more necessary computational power is.
Today, crypto miners employ crypto mining software and powerful computer chips like field-programmable gate arrays (FPGAs) or specialized application-specific integrated circuits (ASICs) to mine cryptos. Some other miners bundle their computing resources in mining pools and share the earned revenue for the newly mined block.
Now, cryptojacking is an illegal way of crypto mining. Hackers don’t employ any of their own resources. Instead, they steal the computing power of an unsuspecting user by deploying cryptojacking malware onto the victim’s platform.
Here, cryptojacking malware is a malicious code that illegally mines cryptocurrency on a device without the user’s knowledge or permission. It can be a simple JavaScript code embedded in a website or malware embedded locally on a device.
Hackers leverage these malicious codes via different methods, like attaching them on webpages and online ads that users might unknowingly click on or installing them on the victim’s computer with social engineering techniques.
Hackers like to target these devices for cryptojacking attacks:
Three major types of cryptojacking occur: in-browser cryptojacking, in-host cryptojacking, and in-memory cryptojacking. Let’s look at all three.
An average computer might be unable to mine cryptocurrencies. But thousands of average computers connected together through the internet could do the job easily. Browser-based or in-browser crypto mining tries to do just that. It simply uses a website visitor’s computer to mine cryptocurrency while they browse.
Here, hackers use ready-to-mine scripts from service providers like Coinhive or CryptoLoot, and inject the code into a website’s HTML source code.
As long as the victim remains online, the mining happens. In-browser cryptojacking becomes profitable when a user remains on a website longer than 5.53 minutes. As a result, it's widely found in free movies or gaming websites.
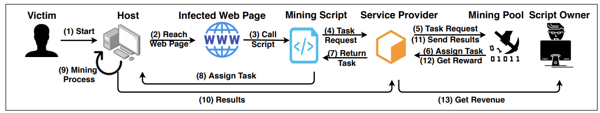
Source: SoK: Crypotjacking Malware - arXiv
Browser-based cryptojacking saw a massive decline when CoinHive, a major crypto mining script provider, shuttered during the crypto market downturn in 2019. However, researchers keep finding new crypto mining scripts and websites that use them intentionally or unintentionally.
In this type of cryptojacking, hackers install crypto malware like traditional Trojan horses. For example, an attachment of a phishing email can infect a computer by loading crypto mining code directly into the disk.
Apart from crypto mining scripts, attackers also modify several plug-and-play style mining applications like XMRig to illegally mine cryptos.
Hackers deliver the malware to the host system using vulnerabilities or social engineering techniques or as a payload in an unintentional download (the drive-by-download technique) on the host’s device.
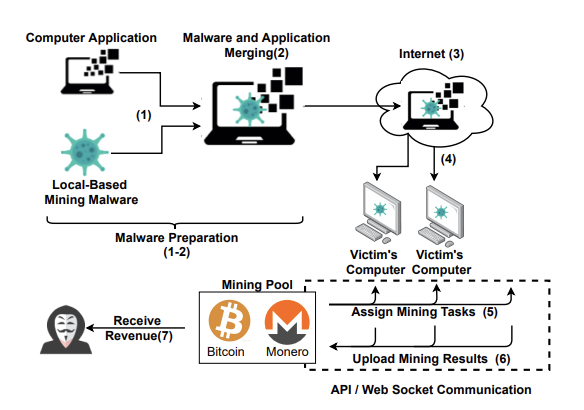
Source: SoK: Crypotjacking Malware - arXiv
For instance, hackers recently disguised their crypto mining malware as a desktop version of the Google Translate app. It was downloaded by thousands of users searching for Google Translate for their personal computers (PCs). However, once installed, it put in place a sophisticated setup to mine Monero cryptocurrency without the user’s knowledge.
In-memory cryptojacking uses the same methods of infection as host-based cryptojacking. However, cryptojacking malware is usually fileless malware and runs on random access memory (RAM). It misuses legitimate local applications or preinstalled tools.
As a result, the cryptojacking script doesn’t leave any footprints in the system, making it difficult to detect and remove. Once attackers are inside a system using fileless malware, they leverage the access to escalate their privileges in the victim’s network and gain a large pool of the victim’s central processing unit (CPU) resources to illicitly mine cryptos.
Since attackers can gain command and control with this method, a fileless cryptojacking can be converted to a ransomware attack, too.
Mehcrypt, for instance, is fileless cryptojacking malware. It abuses several legitimate applications, like notepad.exe and explorer.exe, to carry out its cryptojacking routine.
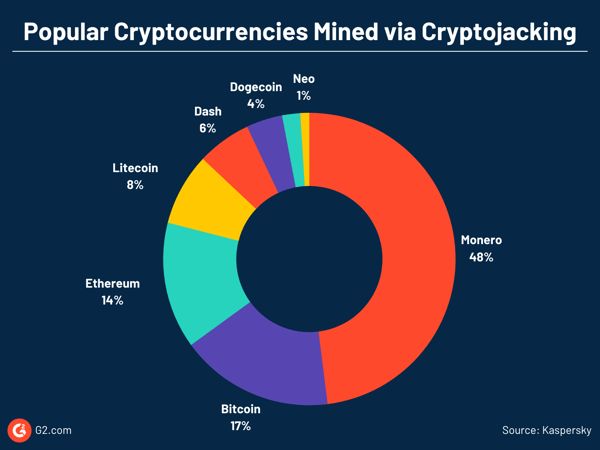
From the early days, cryptocurrency miners developed novel ways of getting additional computational power to mine cryptos that reduced their burden. One of those ways was browser-based crypto mining.
When it was first introduced in 2011, browser-based crypto mining was promoted as an alternative to in-browser advertising. And why wouldn’t people not like it? Instead of seeing intrusive ads on websites, you get a clean browsing experience in return for lending your computer to crypto miners. Simple, straightforward – sounds legal, right?
That’s what lots of other people thought in the beginning. A number of crypto enthusiasts and website owners used in-browser mining by adding mining scripts to their websites. However, browser-based mining was soon abused by hackers and cybercriminals. It became particularly notorious after the launch of Coinhive in 2017.
Coinhive was a crypto mining script provider. In 2017, it released a simple JavaScript that mined Monero (XMR), a Bitcoin-like cryptocurrency, by employing in-browser crypto mining.
Generally, JavaScript is automatically executed when a web page is loaded. It’s platform-independent and runs on any host – PCs, mobile phones, tablets – as long as the web browser running on the host has JavaScript enabled.
As a result, any website could embed the Coinhive JavaScript on their site and make the website visitor’s computer mine for them. Coinhive took 30% of the mined Monero as their fee, while the web page owner took the rest.
The easy, scalable, and low-effort method to roll out crypto mining to a large user population without additional investments made it disruptive. A large number of crypto enthusiasts readily adopted its code.
However, while Coinhive’s business model was touted as legal, soon enough, its code was abused. Some website owners hijacked users’ processing power without their permission to mine XMR using the Coinhive script.
Aside from website owners, malicious actors hacked and embedded the crypto mining code on high-traffic websites. They also installed the script on browser extensions like Archive Poster and website plugins like Browsealoud.
Through these methods, Coinhive’s code found its way illegally to popular websites of companies like Showtime, The Los Angeles Times, Blackberry, and Politifact. They ran in-browser crypto mining without permission and sometimes without the website owner’s knowledge, effectively hijacking the site and the user’s computer resources. Even the websites of the US, UK, and Indian governments’ websites were found to be affected by these cryptojacking attacks.
It should be noted that mining cryptocurrencies with the computing power of others is not considered illegal when a clear notification of activities is shown and the possibility of opting out exists for users. However, most in-browser crypto mining lacks these and is therefore considered illegal.
The rising instances of illicit crypto mining from 2017 brought cryptojacking to mainstream attention. Cybercriminals started using not only illegal browser-based crypto mining but also employed malware and other methods for illegal crypto mining.
Consider this. In 2009, a PC with an Intel Core i7 processor could mine around 50 bitcoins daily. But today, we need specialized mining rigs like ASIC systems to mine cryptos like Bitcoin.
Further, many cryptocurrencies also have limits on how many coins can be mined and the reward that miners get. Add to this mixture soaring energy prices. A single bitcoin requires 811.90 kilowatt-hours, equivalent to the average amount of energy consumed by an American household in 28 days. All this makes crypto mining a costly affair. Today, mining Bitcoin at home is not even an option.
In such a situation, turning a profit from crypto mining with legitimate resources could be difficult. As a result, hackers try to offload the cost to others by hijacking a victim’s system.
Forewarned is forearmed. It’s better to know the dangers of cryptojacking and be prepared than fumble when you face an actual attack.
Unlike many other cybersecurity threats which announce their presence, cryptojacking succeeds in complete silence.
Amal Joby
Cybersecurity Research Analyst, G2
What’s more concerning is attackers today target devices with more processing power rather than personal devices. Some examples are enterprise cloud infrastructures, servers, a large number of inadequately protected IoT devices, or Docker and Kubernetes containers. With this, the attackers aim to obtain more profit in less time.
For enterprises, this has wide-ranging implications. For every dollar made from cryptojacking, the victim gets billed $53. The risk doesn’t stop with inflated bills. Once inside the enterprise infrastructure, the attackers can leverage their access at any time to carry out other dangerous cyber attacks like ransomware and supply chain attacks.
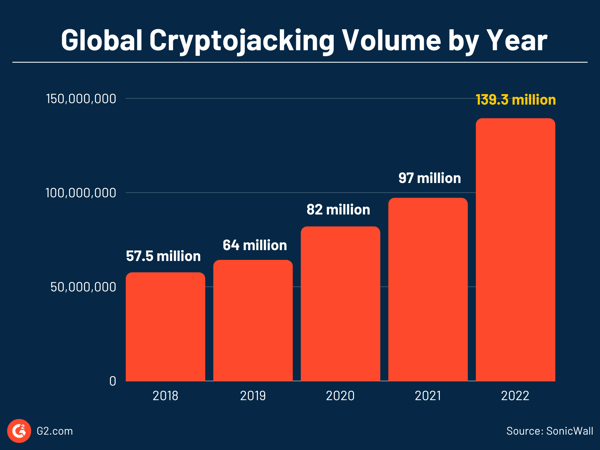
Cryptojacking attacks are often hidden but not unidentifiable. Try some of these methods to detect cryptojacking attacks.
If you notice the following signs on your PC or mobile device, your device may have been cryptojacked.
Cryptojacking causes your device to significantly slow down or crash very often. If you start noticing any unusually poor device performance, scan your system using antivirus software to see if you find any cryptojacking malware.
Another telltale sign of cryptojacking is overheating. Since cryptojacking consumes too much processing power, it easily overheats a system and drains the battery. You might notice fans in your system running faster than usual to cool the device. Or your mobile phone battery might show poor performance and drain rapidly due to overheating.
Another noticeable symptom is high CPU usage. Computers keep records of all the running applications in the system. If you notice a spike in CPU usage while doing a small task or browsing an innocuous website, it may be because of cryptojacking.
To check CPU usage:
You should also check if there’s an application that has increased internet traffic more than normal, which could indicate in-browser mining. To check this:
Note that criminals have come up with sophisticated evasion techniques to hide spikes in CPU usage or internet traffic.
Detecting cryptojacking might be difficult if companies have lower visibility into their cloud usage. However, businesses can try to work around this.
Most of the cyberattacks on the cloud originate from the misconfigured cloud, so audit your access controls. Any insecure or misconfigured entry to your cloud environment can be further investigated to see if there’s been any malicious activity like illicit crypto mining.
Network logs keep track of traffic to and from your cloud and show you the current state of the network and who's connecting from where. Analyze these records. You’ll recognize any irregular network behavior or a sudden spike in traffic. This could be a sign of an illicit crypto miner running on your cloud environment.
Inflated cloud bills are signs of either legitimately increased usage of cloud resources from your end or someone stealing your cloud resources for their profit. If you don’t have any cloud mismanagement on your end, investigate any spike in cloud bills to see if it’s related to cryptojacking.
To be clear, all these methods tell you if your cloud has been compromised in any way. Further analysis of any malicious activity should be done to find out if the compromise is due to illegal crypto miners or any other cyber attack.
Prevention is better than cure, so use these practical tips to safeguard your systems against cryptojacking attacks.
For enterprises, preventing cryptojacking attacks goes beyond covering these basic steps. Adopt the following security practices to protect your IT assets against any illicit crypto mining.
Cryptojacking attacks are becoming more prevalent and difficult to detect even as crypto prices fluctuate. Hackers are getting more sophisticated with their infection and evasion techniques, but prevention is the key. Implement the security practices shared here and stay one step ahead of crypto thieves.
Want to level up your system security? Explore threat intelligence software to keep your security team updated on emerging malware, zero-day vulnerabilities, and exploits.

Find the right web application firewall to block and protect against malicious traffic to your network.
Soundarya Jayaraman is a Content Marketing Specialist at G2, focusing on cybersecurity. Formerly a reporter, Soundarya now covers the evolving cybersecurity landscape, how it affects businesses and individuals, and how technology can help. You can find her extensive writings on cloud security and zero-day attacks. When not writing, you can find her painting or reading.

Find the right web application firewall to block and protect against malicious traffic to your network.
Cryptocurrency, also known as crypto-currency or crypto, is a form of virtual or digital money...
 by Sagar Joshi
by Sagar Joshi
Imagine if a 12-year-old boy received $1000 from his grandmother, invested it, and became a...
 by Claudia Jeffrey
by Claudia Jeffrey
In the world of crypto, coins speak louder than words.
 by Washija Kazim
by Washija Kazim
Cryptocurrency, also known as crypto-currency or crypto, is a form of virtual or digital money...
 by Sagar Joshi
by Sagar Joshi
Imagine if a 12-year-old boy received $1000 from his grandmother, invested it, and became a...
 by Claudia Jeffrey
by Claudia Jeffrey
Never miss a post.
Subscribe to keep your fingers on the tech pulse.



