What Is Cloud Encryption? How It Works, Benefits and Examples
G2
MAY 31, 2023
Data security and protection are the secrets to success for many businesses, and cloud data security providers are constantly evolving to offer the most advanced features.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

 cloud-encryption
cloud-encryption 
G2
MAY 31, 2023
Data security and protection are the secrets to success for many businesses, and cloud data security providers are constantly evolving to offer the most advanced features.

Salesforce
DECEMBER 5, 2023
With every custom application , cloud service, customer account, proprietary technology, and remote work log-in, your risks multiply. Several key factors are behind this staggering increase: Remote and hybrid employees working on insecure Wi-Fi networks or cloud storage solutions with their personal devices. trillion in 2025.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Veloxy
MARCH 5, 2024
Both services offer substantial email management features with Gmail using labels and automated sorting and Outlook using folders, rules, and filters, coupled with robust security features like end-to-end encryption and spam filtering. Outlook and Gmail both equip their users with robust security features.

Martech
DECEMBER 7, 2021
Mobile analytics and attribution platform AppsFlyer today announced the launch of their new Privacy Cloud, developed in collaboration with Intel. App stores and developers and ad networks will be able to define their own Privacy Cloud Applications. The post AppsFlyer announces new Privacy Cloud appeared first on MarTech.
SaaStr
NOVEMBER 4, 2020
So finally, after likely trillions of minutes of sessions, Zoom is rolling out end-to-end encryption. Because of course “end-to-end encryption” sounds like something you’d want, and it sounds like a big upgrade. No cloud recording? And each Zoom session was already highly encrypted before this.

Sales Pop!
NOVEMBER 11, 2021
Data Encryption. Data in transit is encrypted and securely transmitted using the latest SSL (secure socket layer) technology. Data at rest is encrypted by our cloud provider AWS (Amazon Web Services). AWS utilizes the industry-standard AES-256 encryption algorithm for the encryption of data on the server.

PandaDoc
MARCH 22, 2024
These online platforms leverage robust encryption and access controls to safeguard intellectual property. Learn more about PandaDoc VDR Schedule a demo and get acquainted about cloud-based, top-notch security and easy-to-use deal desk. This is where virtual data rooms (VDRs) come in.

Salesforce
MARCH 9, 2022
As a former executive in the federal government, my career focused on modernizing the government’s legacy IT by pushing for secure, modern technologies like cloud computing. When I started in 2009, cloud computing wasn’t well known or widely recognized. billion , in total contract value, on cloud computing services.

Sales Pop!
NOVEMBER 16, 2022
In essence, it’s just an advanced cloud-based repository for sensitive documents. For instance, custom file sharing and cloud server solutions are insufficiently secure for business documents. In comparison to virtual data room providers, there is a lack of good encryption. How Virtual Data Room Works.

Search Engine Land
OCTOBER 3, 2023
Cloud storage misconfigurations Data stored in cloud-based services can be inadvertently exposed if the storage settings are misconfigured. Others may interact with third-party services or APIs, such as saving content to cloud storage. If improperly configured, these extensions can expose PII content.

PandaDoc
MARCH 1, 2024
Key takeaways A virtual data room (VDR) is a cloud-based repository for storing and sharing confidential documents between parties participating in the mergers & acquisitions process. In the past, M&A data rooms used to be physical rooms in the seller’s office or on their business premises.

Veloxy
DECEMBER 13, 2022
Any data stored on mobile devices should also remain encrypted and be secure against attacks like this. One of the ways that you can do this is by ensuring that you are utilizing a cloud-based platform. The right mobile device management strategy should include a comprehensive and inclusive security solution.

Salesforce
SEPTEMBER 7, 2023
Teach me how +1,100 points Trail Build a Data Strategy for Data Cloud Data strategy with trust as a key tenet You need to also consider and address the AI trust gap. Use best practices , such as data encryption, multi-factor authentication and identity and access management to ensure safeguard data security.

Sales Pop!
NOVEMBER 5, 2021
There are now several Cloud providers available, in addition to Amazon Web Services (AWS). Many didn’t know it at the time, but alongside Amazon, Jeff Bezos was also building Amazon Web Services, focused on supporting companies in utilizing the Cloud for easily building an infrastructure. Why have we done so? Original Data Center.
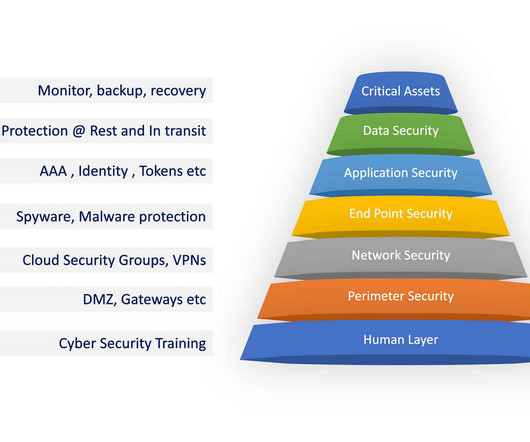
Search Engine Land
OCTOBER 6, 2023
Enhancements in infrastructure, including CDNs, CI/CD and DevOps practices, cloud solutions, microservices architecture, and containerized hosting, contribute to the robustness of the deployed tech stack. Cloud solutions are easy to scale based on the demand of business. This includes: Using HTTPS.
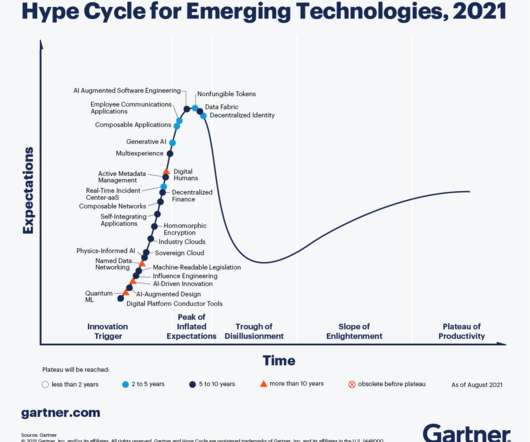
Smarter With Gartner
AUGUST 22, 2021
Other technologies in that fall into the engineering trust bucket include sovereign cloud, homomorphic encryption and data fabric. Other emerging technologies that fall under accelerating growth include multi-experience, industry cloud and quantum ML. Theme 2: Accelerating growth. Theme 3: Sculpting change.

Sales Pop!
AUGUST 17, 2021
Amazon stores the “palm signature” into the cloud, and links the shopper’s hand to its credit card. Amazon encrypts the data as a unique palm signature to ensure secure payments. Then, the biometric info is sent to a custom area in the cloud. The computer will code the unique veins and ridges of the hand.
Heinz Marketing
JANUARY 24, 2024
Solution: Investing in strong cybersecurity measures, including encryption, access controls, and regular security audits, is vital. Solution: Leveraging cloud-based CRM solutions and scalable big data platforms can help manage the volume and complexity of the data.

Heinz Marketing
MARCH 12, 2023
Skai is an innovative, cloud-based, business intelligence platform that empowers users to make data-driven decisions for their marketing campaigns with ease. You can import data from spreadsheets, databases, cloud storage, and more. While browsing the sea of options, there was one that caught my eye – Skai.

Salesforce
JANUARY 25, 2024
These recordings are then stored, logged on a computer or in the cloud, and can be used by sales teams for analysis. Data management and security : Look for a tool that allows you to store call recordings and information in the cloud and locally (for greater business need flexibility). Want to take the #1 CRM for a test drive?

Salesforce
JULY 10, 2023
Get started with AI Cloud Salesforce Professional Services can help you set the right foundation for success with our new package, AI Coach. It is imperative to safeguard your company’s sensitive customer data with a trusted AI platform, such as Salesforce’s AI Cloud , built on the Einstein GPT Trust Layer.

Heinz Marketing
OCTOBER 23, 2022
Wrike is a comprehensive cloud software tool that can support multiple functions within your org including marketing, project management, IT, and professional services. With enterprise-grade security, you can use smart automations to protect any data, from role-based access, encryption key ownership, and more.

Hubspot
MAY 3, 2019
Fortunately, there are cloud integration platforms that can connect your distinct cloud-based applications together, let you manage their data, and even automate your business processes all in one interface. Read on to learn what exactly cloud integration is and the best cloud integration platforms on the market, according to G2.

ConversionXL
OCTOBER 21, 2019
No database administration; No limitations; Quick imports; Process terabytes in seconds; Data stored in EU or United States; Encryption; Access control; Two-step verification; Data-loss prevention; Integration with other Google tools; $300 in test credits; Huge community; Educational resources (courses, labs, etc.).

SalesHandy
NOVEMBER 9, 2020
Also, all shareable and non-sharable files are stored in a TLS encrypted format by default. Encryption isn’t enabled by default, but can be set up to encrypt your files in TLS. G Suite Pricing: Apart from cloud storage capacity, we don’t see much difference in the pricing tiers on G Suite.

Salesforce
SEPTEMBER 12, 2023
Masked data has no value to hackers, and unlike encrypted data, which needs to be decrypted, doesn’t need to return to its original form. It can reduce risk in both on-premises and cloud environments , and it is one of the most important tools that helps keep your data secure — building trust with your customers and partners.

Salesmate
JULY 7, 2020
You should also have the latest versions of all documents and templates stored in the cloud, which employees can access at any time. In addition, everyone should be accessing the internal network via a VPN connection, which encrypts the data before it’s transmitted across the internet to protect sensitive information from hackers.

Hubspot
JUNE 14, 2018
It’s an encrypted “packet” associated with a document. Digital signature software will create a condensed version of a document -- called a hash -- which will be encrypted using a key in a signatory certificate. This encrypted “hash” is the signature. A digital signature is not the same as an electronic signature.

Hubspot
SEPTEMBER 6, 2018
Software wallets are installed on your computer, but they’re more secure than mobile or web wallets because they can encrypt your private key and account recovery phrases. You can store all your coins, keys, and passwords on it, use it to encrypt your data on the cloud, and get your own personal recovery seed, in case you ever lose it.

Hubspot
MARCH 21, 2018
Unlike other email accounts, you can use your Gmail address to log into and manage your YouTube account, as well as collaborate on shared documents and spreadsheets right from a cloud-based Google Drive. This is the first of the lesser-known free email accounts to make our list, but it holds a lot of potential for businesses.

Hubspot
JANUARY 3, 2022
For instance, HubSpot Payments comes with layers of security meant to protect payment information as well as encrypt and tokenize buyer payment credentials so unauthorized people aren't able to access a customer's information. Zoho offers a cloud-based sales CRM with subscription billing software. CRM Payment Processing.

Highspot
MAY 19, 2020
You may have a policy that only certain machines in your cloud provider are allowed to be reachable from the internet. If you have policies to patch machines, encrypt thumb drives, or prevent passwords and keys being checked into source control, automate them all.

Veloxy
APRIL 26, 2023
Salesforce also offers encryption and two-factor authentication to further strengthen security. Salesforce Service Cloud, a customer service software built on the Salesforce platform, provides a range of features such as case management, knowledge base, chatbots, live chat, email management, and social customer service.
Hubspot
SEPTEMBER 25, 2018
The team chat tool offers a cloud solution that has the same functionality as Slack, starting from $50 per team for each month. RocketChat also has useful features like real-time translation, live chat client, and E2E encryption, making it a Slack alternative that’s definitely worth a look. Mattermost.

Hubspot
DECEMBER 26, 2014
Check out our list below of a few of the top cloud-based backup tools for your computers, phones, and tablets. Launched in 2011, iCloud is Apple''s cloud storage service. According to Ars Technica ''s review , "backup to the cloud does take up a significant amount of time over backing up to the SD card. 6) G Cloud Backup.

SaaStr
APRIL 4, 2019
Join us for a fireside chat between Google Cloud and Zenoss, a leader in software-defined IT operations, as we discuss the most common and emerging challenges facing SaaS companies today for both technical and non-technical backgrounds. Eyal Manor – VP, Engineering @ Google Cloud. Want to see more content like this session?
ConversionXL
FEBRUARY 17, 2021
Only this update to the model is sent to the cloud, using encrypted communication, where it is immediately averaged with other user updates to improve the shared model. All the training data remains on your device, and no individual updates are stored in the cloud.

Salesforce
JANUARY 8, 2024
Phishing attacks are a common way to spread ransomware, a malicious software that infects devices and encrypts data so you can no longer access it. Attackers ask for a monetary ransom in exchange for the encryption key, but they don’t always keep their word. Encryption helps you avoid data theft that can erode your company’s ROI.

Hubspot
NOVEMBER 12, 2015
HelloSign uses SSL encryption during file transfers to keep your documents safe. Google Apps is a package of cloud-based productivity services that make it easy for businesses to collaborate in real time. Recipes link together some of your favorite cloud-based services, and can trigger a specific action based on particular events.

Hubspot
MAY 15, 2015
Like this: You may have heard: Our cloud app had some serious down time last year. We got the laptop back an hour later and the passwords were still encrypted. But marketers do this every day -- it’s one of the things that make marketing shout, "MARKETING!". We let our customers down and paid the price. It had all our passwords on it.

PandaDoc
APRIL 14, 2022
Compared to other Cloud-based drives, DocSend allows you to analyze the behavior of your collaborators. Besides the basic functions offered by DocSend, PandaDoc also allows you to enjoy: Online Document Editor Cloud Storage Integration Non-PDF Docs Support And many other great functions. Ease of use: 5/5. Functionality: 4/5.

Hubspot
MARCH 15, 2012
Although Google didn’t do us any favors with its recent update regarding encrypted search , which in short, means that within your marketing analytics, if a person is logged into Google.com, you will no longer be able to identify which keywords they searched for before they arrived at your website. 7) Cloud Your Website Content.

Hubspot
NOVEMBER 20, 2020
Here are some GDPR-friendly apps to consider adding to your stack: LogicGate Risk Cloud is an agile GRC (governance, risk, and compliance) cloud solution. Boxcryptor makes your cloud storage more secure with encryption for OneDrive, Dropbox, and Google Drive among other providers.

PandaDoc
OCTOBER 3, 2023
Assessing infrastructure helps budget for upgrades like newer CRMs, cloud data storage, and real-time analytics APIs. comprehensive ethical guidelines — basic guidelines — no guidelines Data security and privacy Investigate the tool’s data handling practices, encryption standards, and access controls.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content