75% of top brands fall victim to fraud in Google Search Ads
Search Engine Land
JANUARY 24, 2024
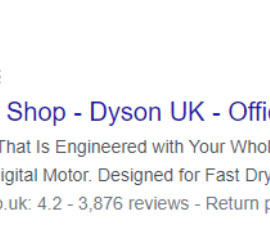
Phishing scams. An example of a phishing scam ad can be seen below: When users click on what appears to be a genuine ad, they are directed through a series of hidden redirects without the user’s knowledge. Over a 90-day period, researchers detected persistent phishing scams on 20 brands from a group of six advertising accounts.










































Let's personalize your content